How to ensure the validity of a figurative trademark ?
Introduction
When considering filing a figurative trademark (logo, image, or graphical sign without words), a fundamental question arises: Are they automatically valid? The answer, under French and European trademark law, is negative. The validity of a figurative trademark depends on specific legal criteria related to its ability to identify the commercial origin of a product or service, as demonstrated in the French Intellectual Property Code, European Union law, recent case law such as the decision in Mercedes-Benz Group AG v. EUIPO (Case T 400/24) of March 19, 2025, and the practices of trademark offices (INPI, EUIPO, etc.).
What is a figurative trademark?
A figurative trademark consists exclusively of graphical elements, designs, logos, symbols, colors, without any independent verbal element (text). It aims to visually protect a sign that distinguishes the products or services of one company from those of its competitors.
Alongside the figurative trademark, we distinguish:
• The verbal trademark: composed solely of words or letters.
• The semi-figurative trademark: a combination of text and visual elements.
This distinction is important because while the validity requirements are generally common under substantive law, they are applied differently depending on the type of sign being filed.
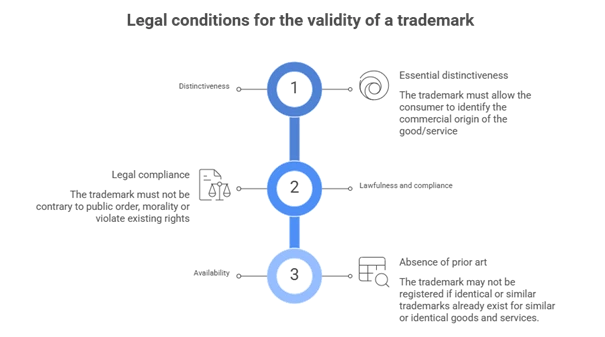
Legal conditions for the validity of a figurative trademark
For a figurative trademark to be considered valid and registered, it must meet several cumulative conditions.
Distinctiveness
Distinctiveness is the primary requirement; the trademark must allow consumers to identify the commercial origin of a product or service. It should not be descriptive, generic, or purely functional.
An arbitrary or stylized logo, unrelated to the products/services, generally presents strong distinctiveness. However, a graphic representing the product itself or an expected feature of the product is rarely considered distinctive.
Legality and public order
As shown in Article L711-3 of the French Intellectual Property Code, the trademark must not be contrary to public order or morals. It must also be lawful and not infringe on existing rights (e.g., personality rights, state arms, international agreements).
Availability
A figurative trademark cannot be registered if identical or similar prior trademarks already exist in the same product or service classes. Thorough searches for prior rights are essential before filing.
Jurisdictional illustrations of refusals or acceptances: the Mercedes-Benz Group AG v. EUIPO Case (Case T 400/24) of March 19, 2025
Facts
In this case, Mercedes-Benz sought to register 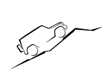
However, the EUIPO partially refused the application due to a lack of distinctiveness for products in Class 12. The Board of Appeal upheld this refusal on the grounds that the sign represented a typical image of an off-road vehicle in a situation and did not contain any distinctive elements to indicate commercial origin to consumers.
EUIPO Tribunal decision
In its decision of March 19, 2025 (Case T 400/24), the EUIPO Tribunal rejected Mercedes-Benz’s appeal, confirming that the sign lacked distinctiveness under the EU Trademark Regulation 2017/1001.
In its reasoning, the Tribunal recalled case law stating that a sign closely inspired by usual representations of the product itself can only be considered distinctive if it deviates significantly from the visual norms of the sector. The drawing in question was not sufficiently different from the usual representations of an off-road vehicle for the relevant public to associate it with a particular commercial origin.
The simplicity and generic nature of the image reinforced the absence of distinctiveness, even though the target public pays attention to the concerned products.
Scope of the decision
This decision illustrates the high level of distinctiveness required for figurative trademarks representing the product or its expected performance.
A drawing that merely represents the product in a conventional or generic manner, without sufficiently unique or unusual elements, is likely to be deemed devoid of distinctiveness and thus ineligible for registration as a trademark.
Strategies to Maximize the Validity of Your Figurative Trademark
Here are some best practices based on practical experience and case law:
• Design an original visual sign: A drawing or logo that deviates from usual product/service representations makes registration easier.
• Combine distinctiveness and creativity: Unusual stylization, distinctive graphic elements, or a unique composition enhance distinctiveness.
• Conduct a prior search: Before filing, an exhaustive search of existing trademarks (both verbal and visual) reduces the risks of opposition or refusal.
• Consider multiple filings: Filing both a verbal trademark and a semi-figurative trademark can strengthen protection, especially for trademarks that rely on both a logo and a name.
Conclusion
Not all figurative trademarks are automatically valid. Their legal validity primarily depends on their distinctiveness, compliance with public order, and availability relative to prior rights. A generic or overly descriptive logo will often be refused registration, while an original and distinctive design will result in solid protection.
To ensure successful registration and safeguard your rights, it is essential to create a strong visual sign and conduct the necessary checks before filing.
Dreyfus & Associés assists its clients in managing complex intellectual property cases, offering personalized advice and comprehensive operational support for the complete protection of intellectual property.
Nathalie Dreyfus with the support of the entire Dreyfus team
Q&A
1. Is a simple logo always valid as a figurative trademark?
No, it must also be distinctive and non-descriptive to be registrable.
2. Can a figurative trademark be refused for reasons other than lack of distinctiveness?
Yes, it can be refused if it contravenes public order, is already used by another party, or does not meet the conditions of representability or legality required by law.
3. Can I modify a figurative logo already filed?
Any significant change generally requires a new filing.
4. Is a drawing very similar to an existing one valid?
No, if it creates similarity with a prior trademark, registration may be refused or the act annulled.
5. Can a color alone constitute a figurative trademark?
Yes, but the color must be specifically claimed and presented with international codes (e.g., Pantone).
This publication is intended to provide general guidance to the public and highlight certain issues. It is not intended to apply to specific situations or constitute legal advice.